How to Setup SSO using Okta
Single Sign-On (SSO) is a user authentication process that allows your users to sign in to multiple applications using the same set of login credentials. This allows ease of use for the end users and ease of management. VIDIZMO offers the most flexible options for you to integrate with a wide range of single sign-on authentication providers, including:
- Directory services such as Azure AD etc.
- Identity Access Management (IAM) services such as Okta, OneLogin, Ping, Centrify,
- Third-party login services such as Facebook, Google, Office 365, X(Twitter), LinkedIn, etc.
With an app model integration for SSO, VIDIZMO makes the integration as easy as enabling/disabling your identity provider from within the platform administrator interface in minutes. Enterprises using Okta as their identity provider can utilize SSO option with VIDIZMO, allowing users to sign in using the same set of credentials.
For more information about VIDIZMO SSO Apps, read Understanding Single Sign-On.
Before You Start
- Okta Developer Account: You must have an active Okta developer account to create an application. Sign up here.
- VIDIZMO Portal: Ensure that you belong to a group where the Management of SSO + SCIM permission is enabled to access this feature.
- Additional SSO Apps:If more SSO Apps have been configured and enabled on your Portal other than Okta SSO, your users will see multiple buttons on the login page allowing them to choose any identity provider of their choice to log in to their VIDIZMO Portal.
- Required Scopes: Ensure the following scopes are exposed by your Okta authorization server:
- Profile (The user's First Name and Last Name are exposed and mapped in your VIDIZMO account in this Scope)
- Email (The user's Email Address is exposed and mapped in your VIDIZMO account in this Scope)
- Phone (The user's Phone Number is exposed and mapped in your VIDIZMO account in this Scope)
- Groups (This is a custom Scope that must be exposed by your Authorization Server. See Adding Custom Scope and Claim to read how to configure it)
- Security Considerations: Enable HTTPS in your VIDIZMO portal, see: How to Configure your Portal to use HTTPS
Configuration in Okta
Creating a New Application in Okta
Firstly, you are required to create an application in Okta in order to configure Okta SSO in VIDIZMO. Following steps show you how to create an application in Okta:
- Go to Okta.com and sign up for Okta account if you don't have one.
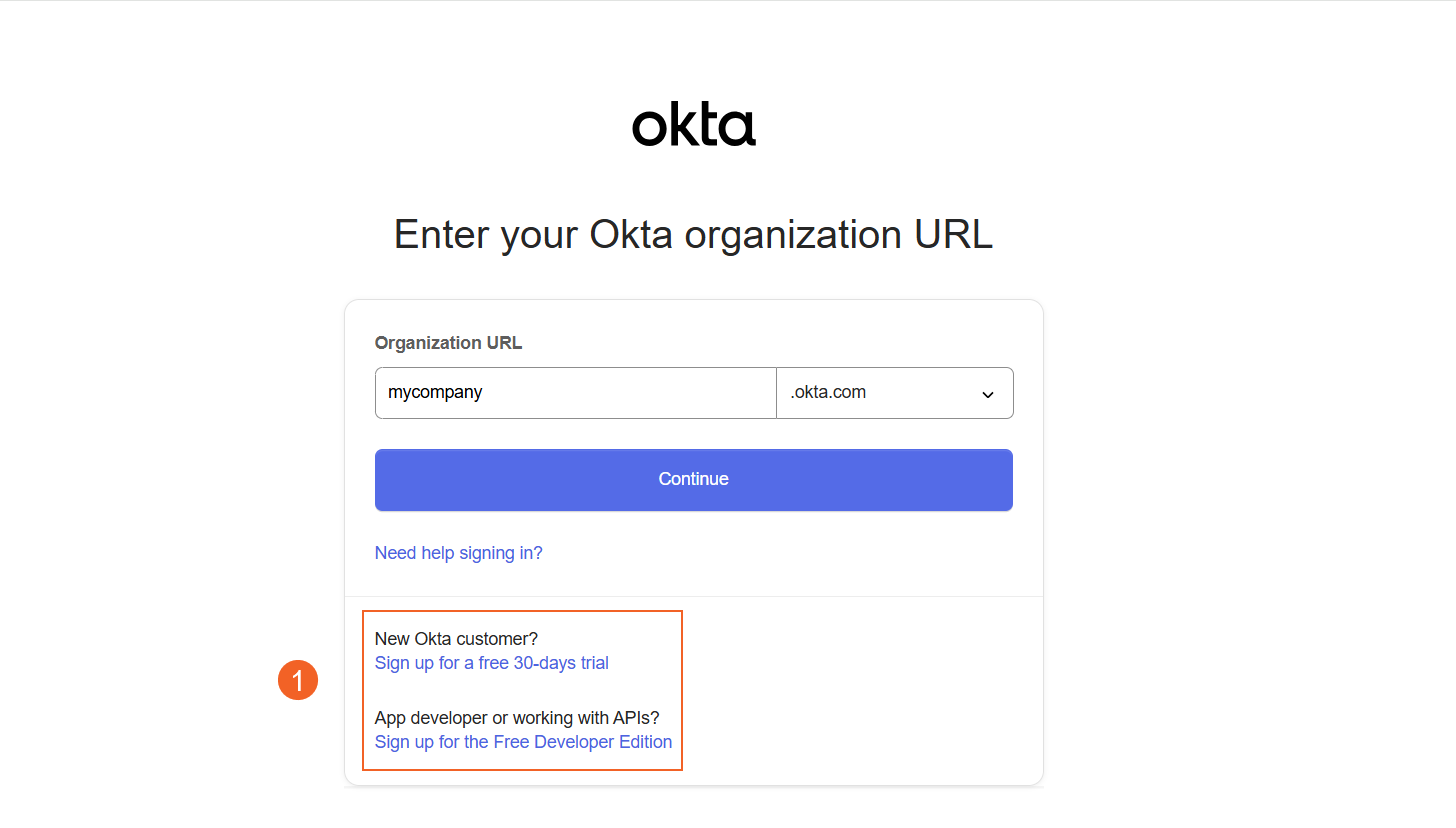
- Enter your ORG URL that you received via email while creating your Okta account. At the Sign In page: i. Enter your email address and password. ii. Click on Sign In.
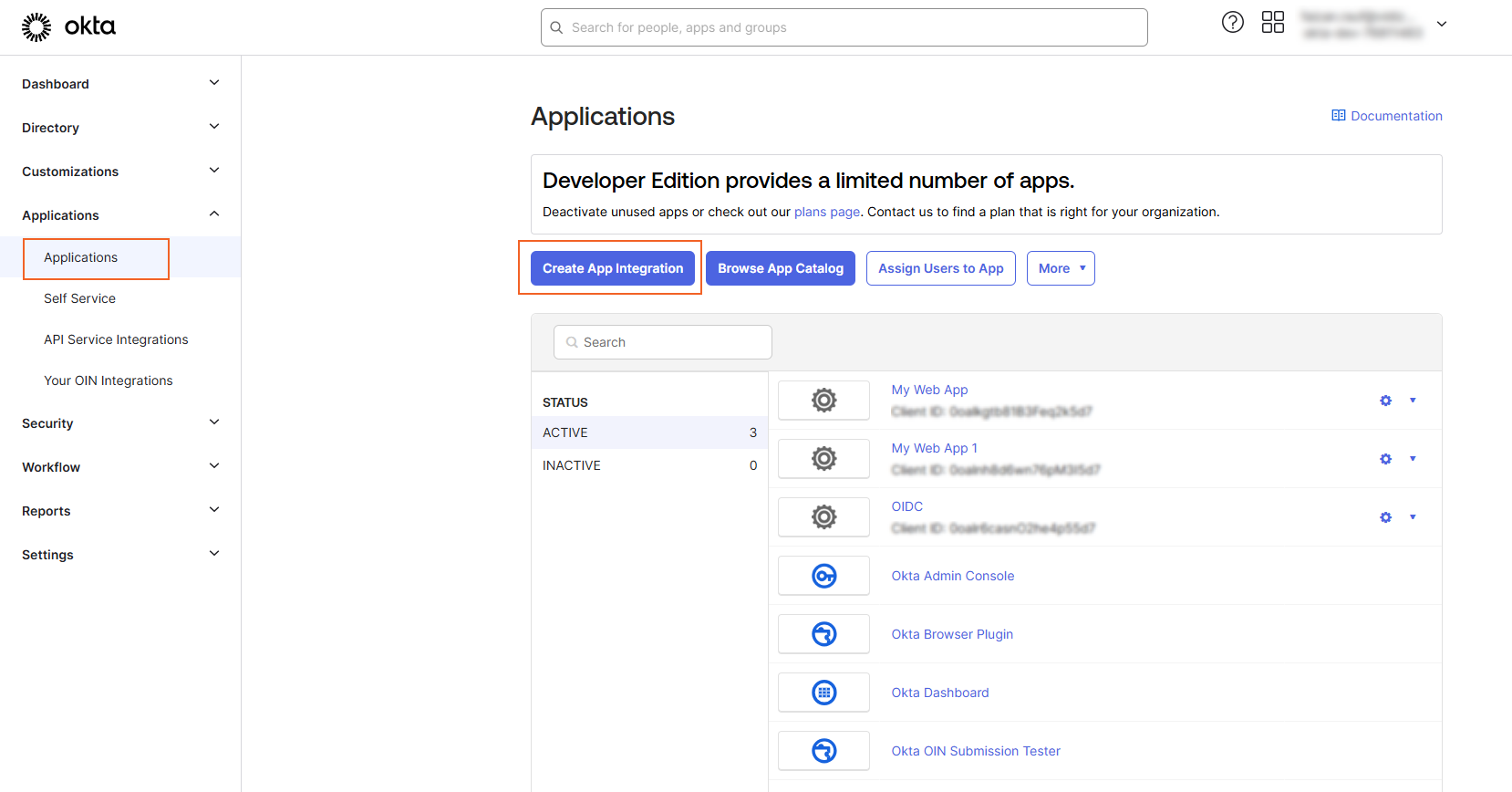
- From the Developer's Dashboard, click on Applications.
i. Navigate to Applications in Okta Dashboard. ii. Click on Create App Integration
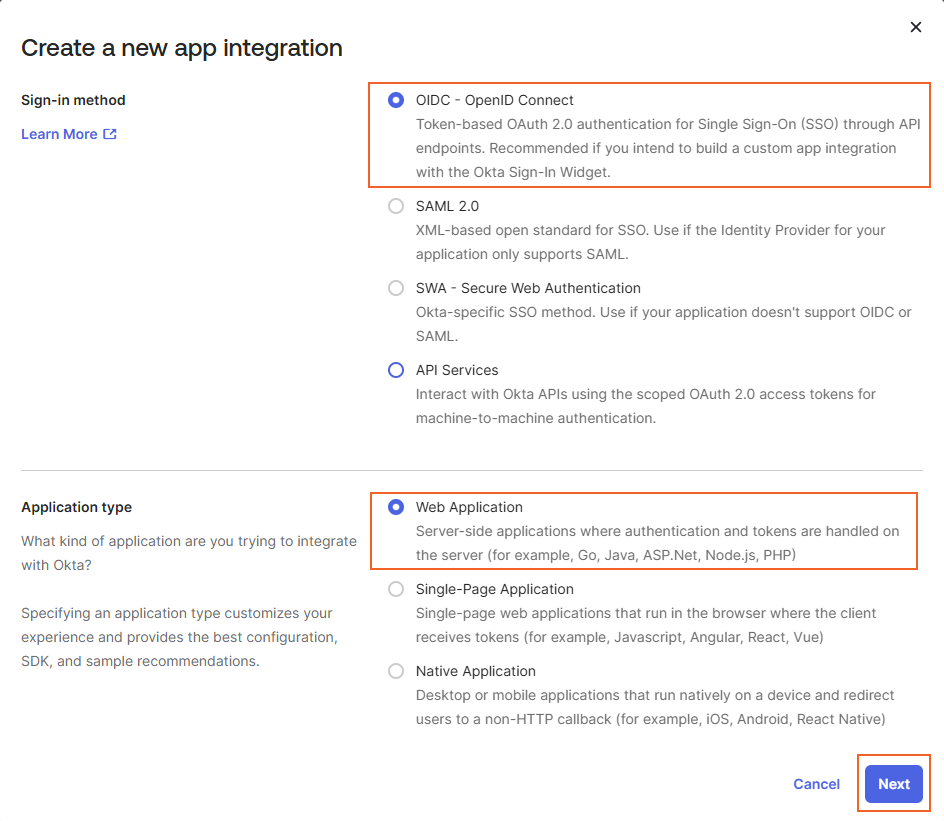
- From the Create a new app integration page: i. Select the Sign-in Method: Choose OIDC - OpenID Connect. ii. Choose Application Type: Web Application iii. Click next.
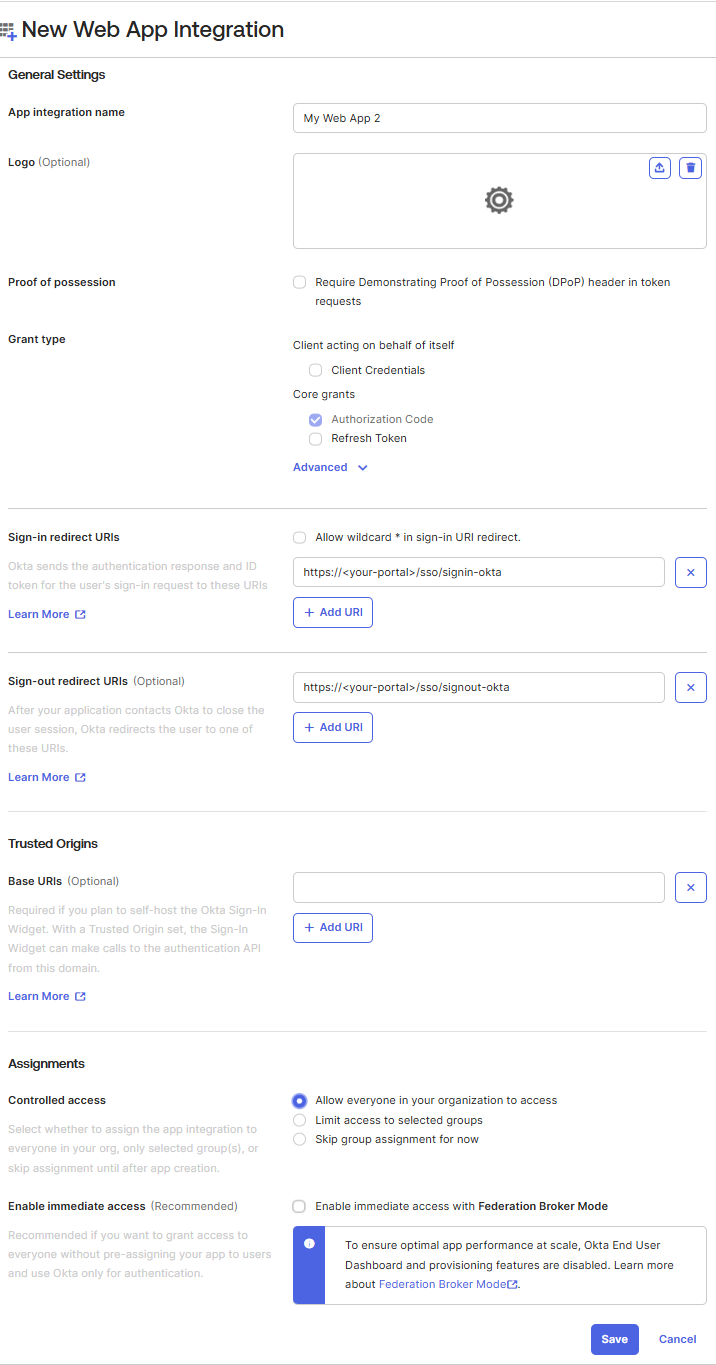
- From the New Web App Integration page:
i. Specify the Name of the Application. ii. Add the logo (Optional). iii. Select the Grant Type (Optional) iv. Specify the following URIs:
- Sign-In Redirect URI:Enter the URI of your portal followed by /sso/signin-okta to specify the endpoint for successful user sign-ins.
Example: https://<your-portal>/sso/signin-okta - Sign-Out Redirect URI:Enter the URI of your portal followed by /sso/signout-okta to define the redirect URI where Okta will send users after they sign out.
Example: https://<your-portal>/sso/signout-oktav. Enter Base URIs (Optional). vi. In Assignment section you can grant the access as per your requirement. vii. Select Save to create the application.
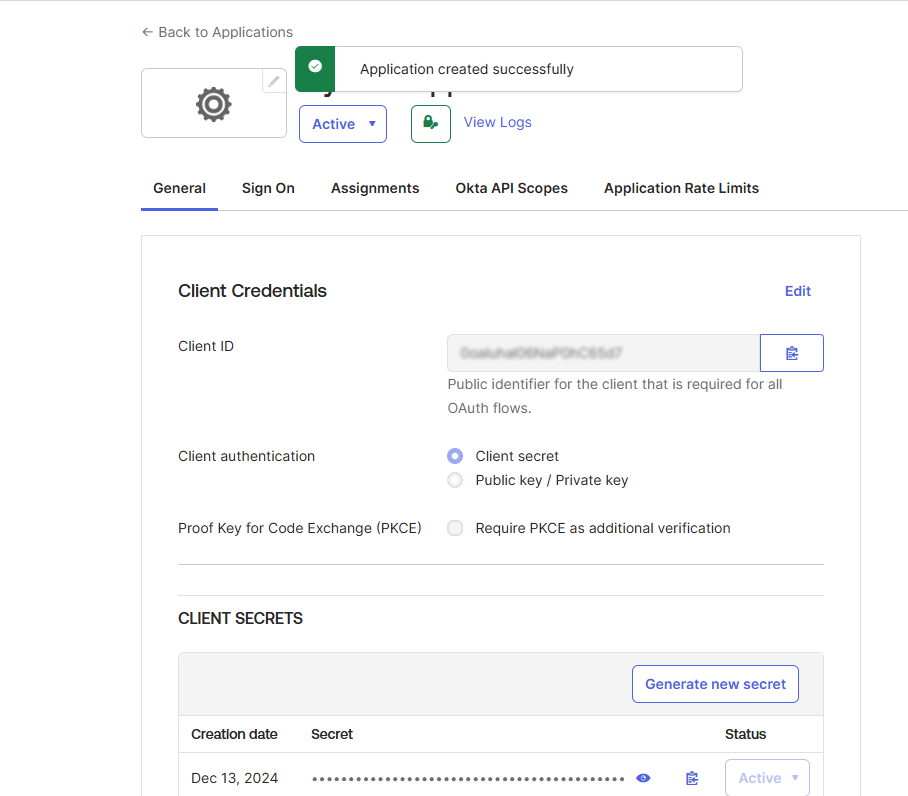
You will be directed to your created application:
Assigning Users and Groups Within the Application
To allow users and groups to sign in using Okta credentials:
- Navigate to the created application's Assignments tab
- Expand Assign to.
- Click on Assign to People or Assign to Groups depending on whom you wish to assign the created application.
- Search and select the relevant users or groups and click Done.
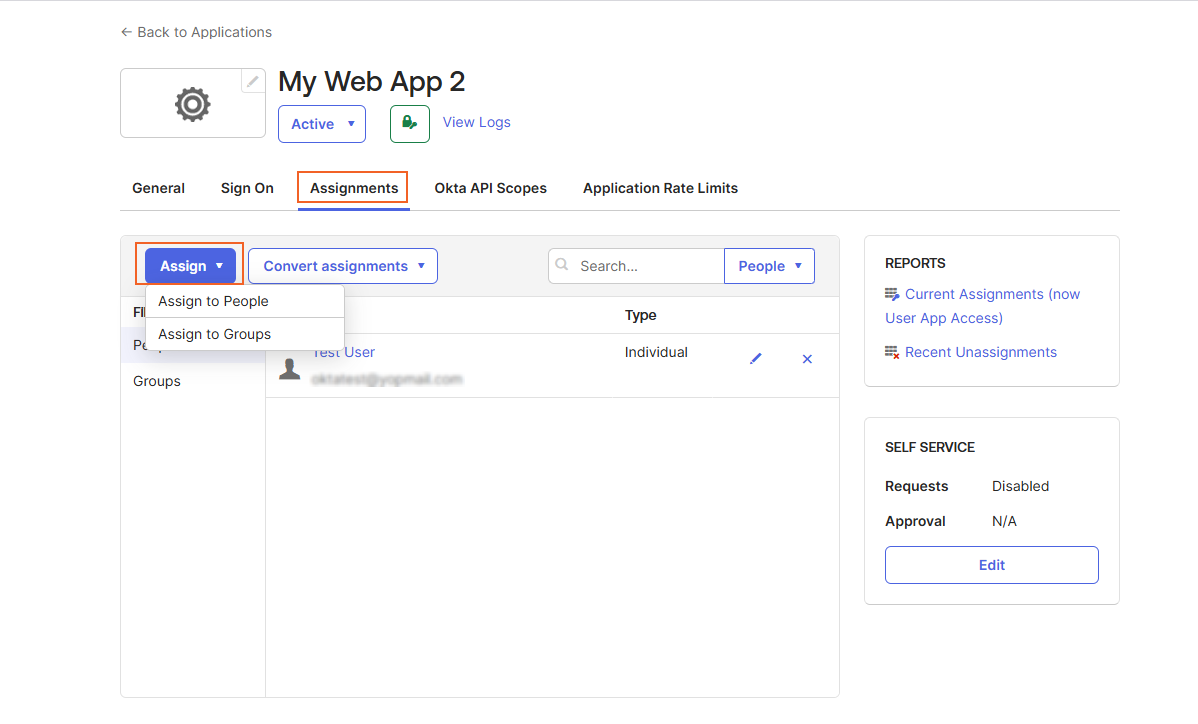
Groups assigned in the Okta application will automatically sync with the VIDIZMO portal, provided that SSO (Single Sign-On) is enabled.
Once you've assigned the application to relevant users and groups, you can move on to the next section.
Adding Custom Scope and Claim
By default, Okta's authorization servers expose a number of scopes during user authentication that allow VIDIZMO to map user information from your identity provider to VIDIZMO. As VIDIZMO synchronizes your Okta groups to your VIDIZMO Portal, it is required that you add a custom Scope named groups in the list of scopes exposed by your authorization server. To know more about Scopes and Claims in Okta, read Key Concepts: Scopes, Claims and, Response Types.
- Navigate to Security and select API.
- Under the Authorization Servers tab, locate the default server and click Edit.
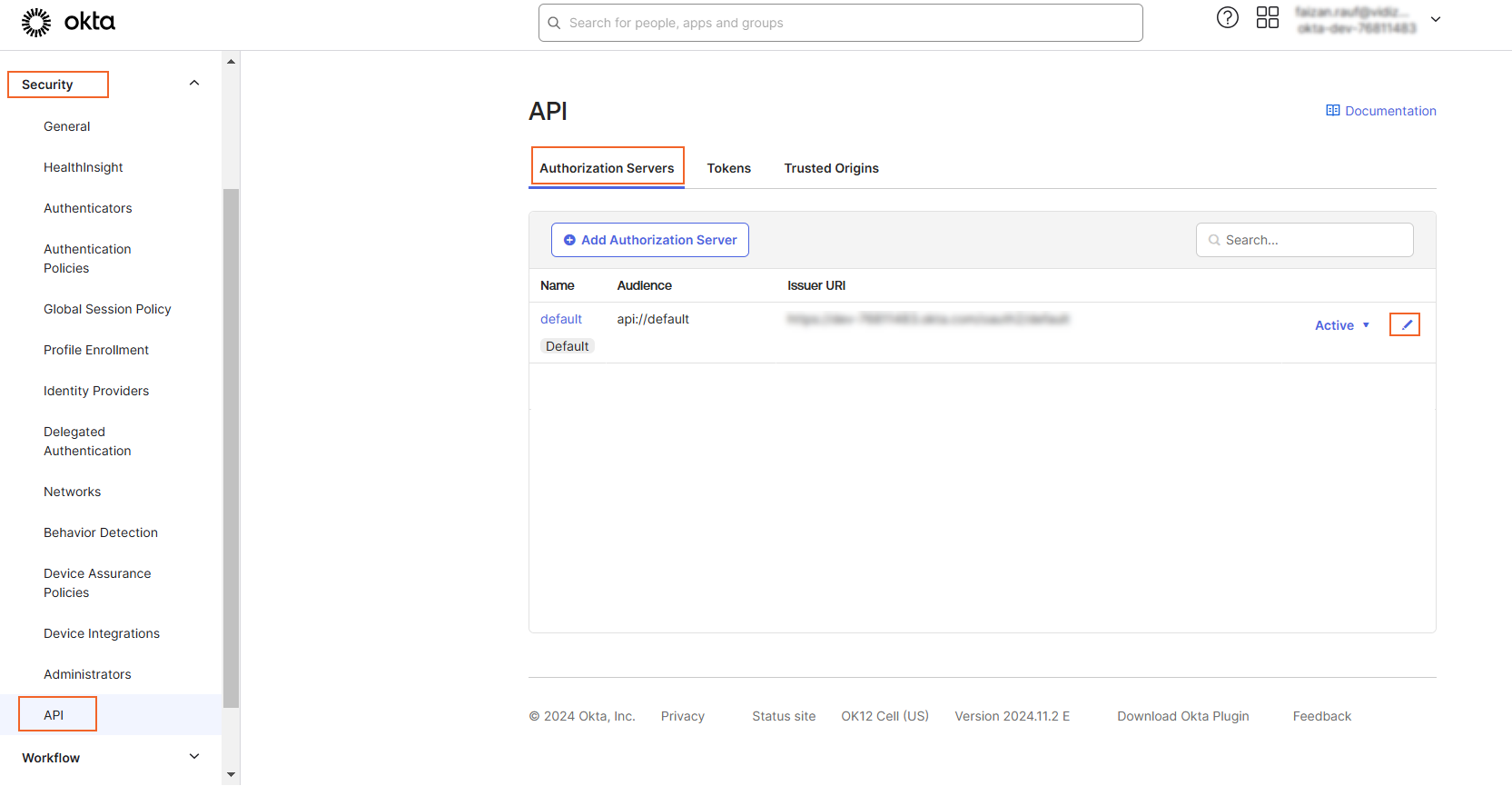
Add Scope:
To synchronize Okta groups with VIDIZMO, add a custom scope follow the steps:
- Navigate to the Scopes tab and click Add Scope.
- A popup Add Scope appears: i. Specify the Name for the scope as groups. ii. Enter a relevant Display phrase as shown. iii. Enter a relevant Description as shown. iv. Enable Options User Consent, Default Scope and Metadata. v. Click on Create to add the Scope.
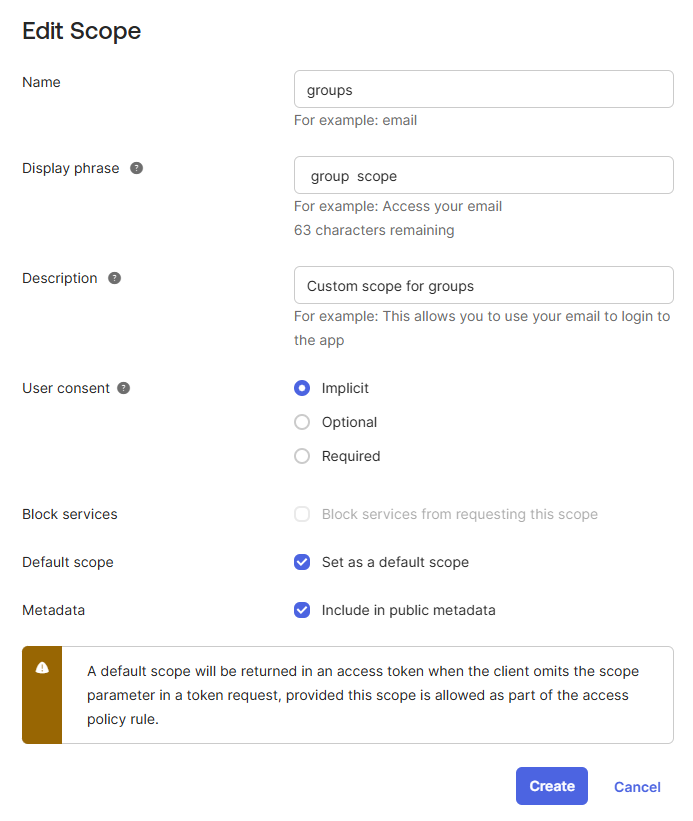
Add Claim:
- Navigate to the Claims tab and click Add Claim.
- A popup Add Claim appears: i. Specify a Name for the Claim ii.Specify Include in token type as ID Token and Always. iii.Select the Value type as Groups from the dropdown. iv. For Filter, select Matches regex and specify .* as the condition. v. Specify the groups scope as created in the previous section under the Include in attribute.
- Click Create to add the claim.
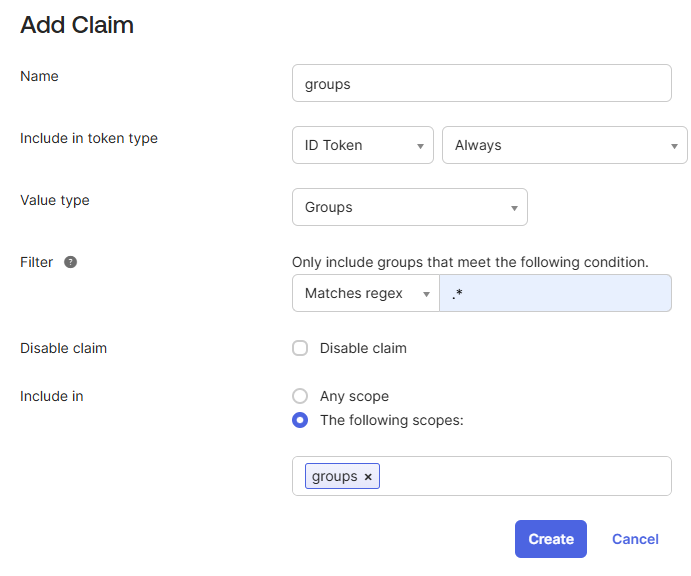
Once done, you'll be able to see the created claim in the list:
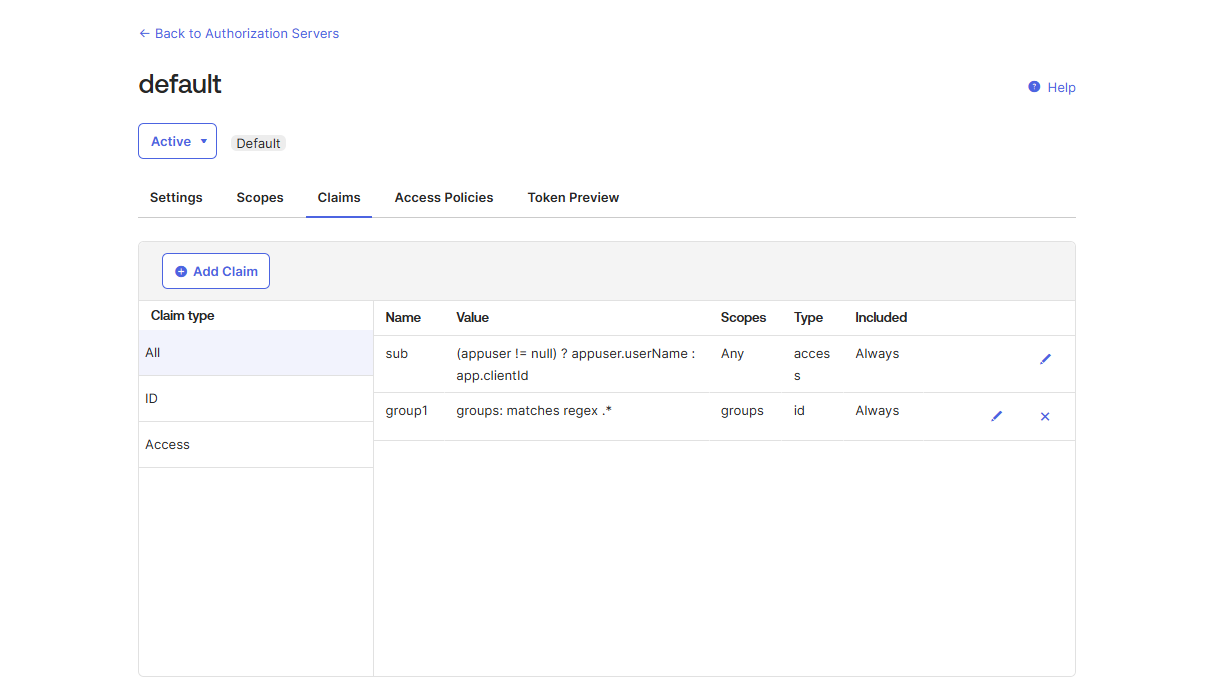
Creating Access Policies
Under the Authorization Servers tab, locate the default server and click Edit.
- Navigate to the Access Policies tab.
- Under the Access Policies tab, click the Add New Access Policy button.
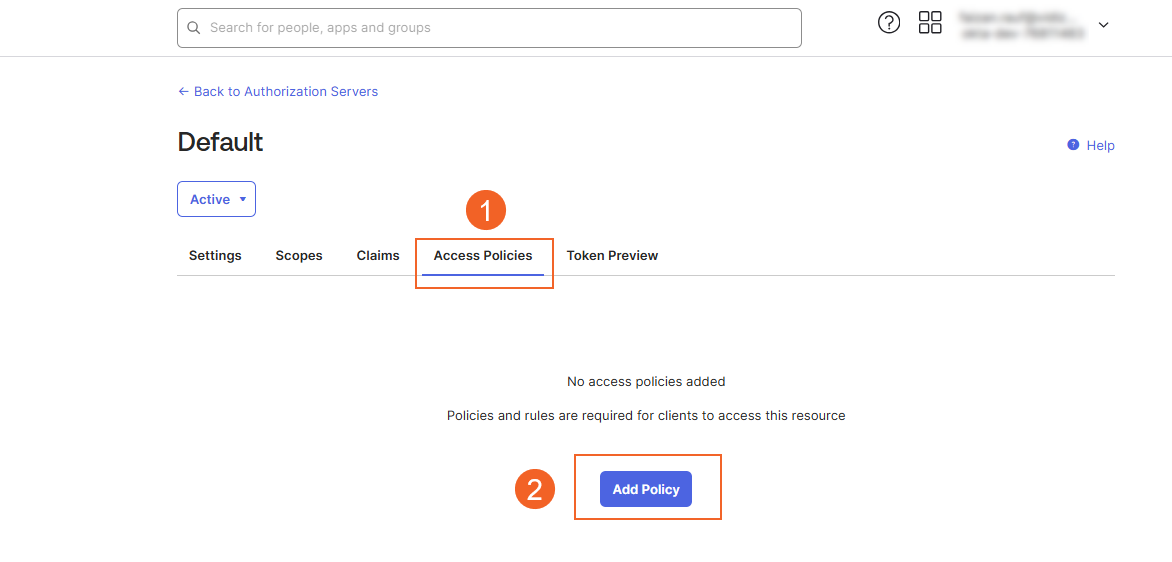
- When the modal appears:
- Enter the Name and Description for the policy.
- Select the Assign To option based on your requirements.
- Click the Create Policy button to save your new policy.
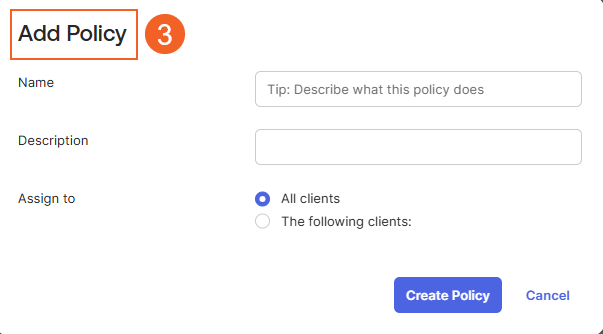
- If you need to define rules for this policy, click the Add Rule button.
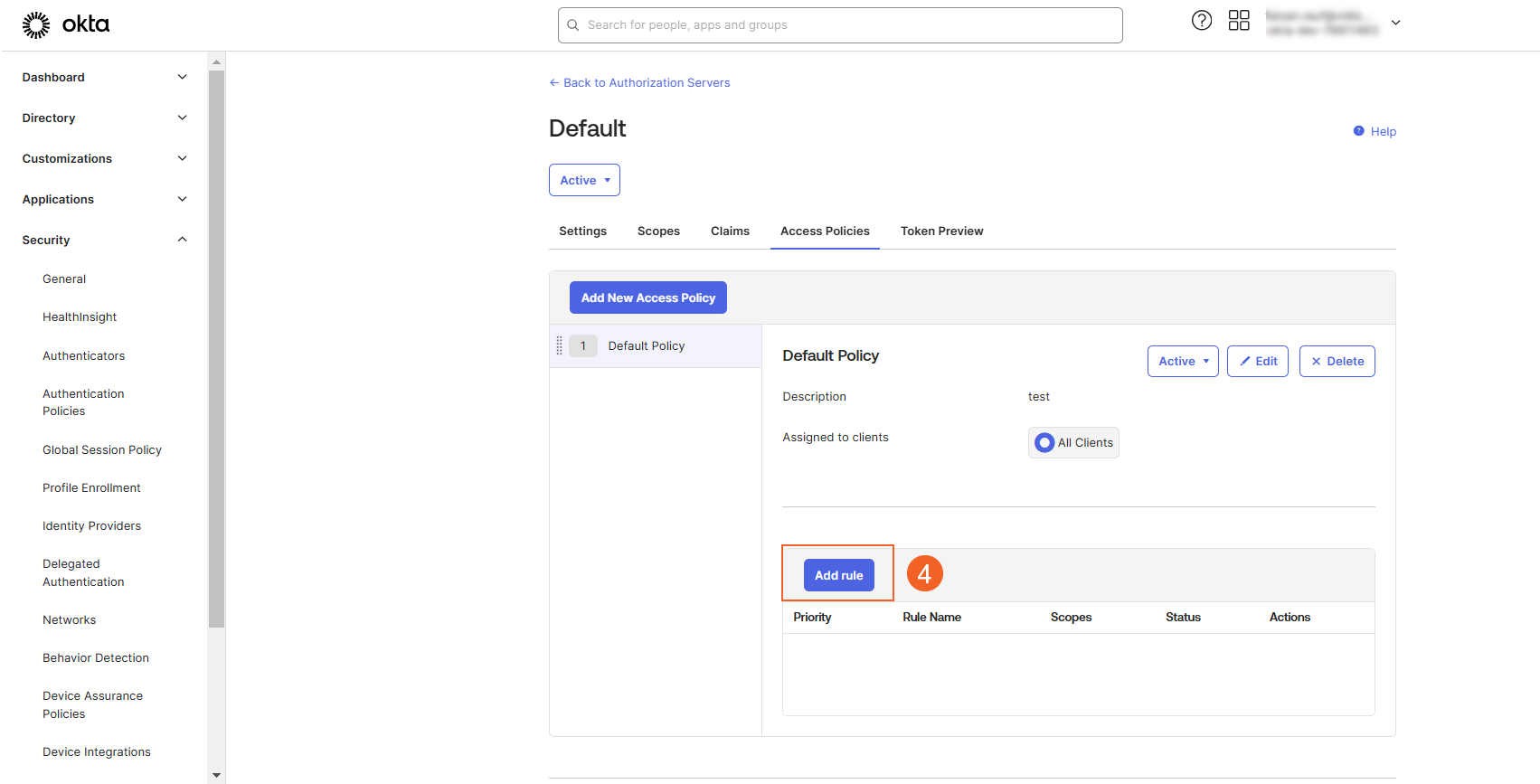
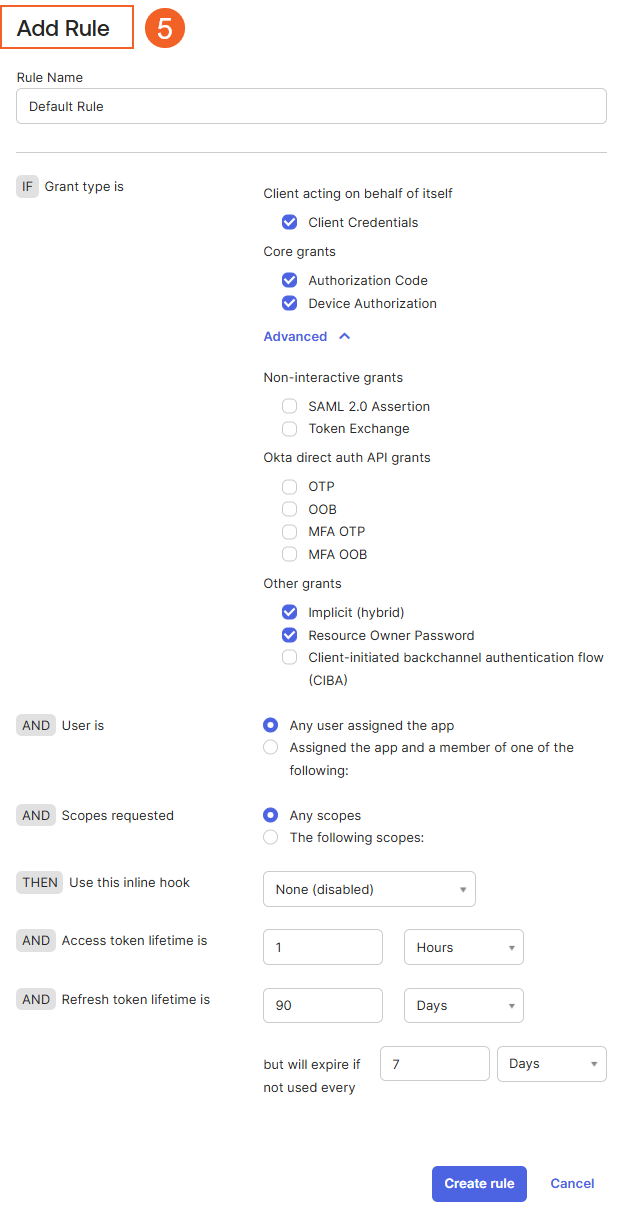
- A modal will open for rule configuration:
- Select the options as required.
- If you are uncertain about specific settings, refer to the screenshot below.
- Click Create Rule to save the rule.
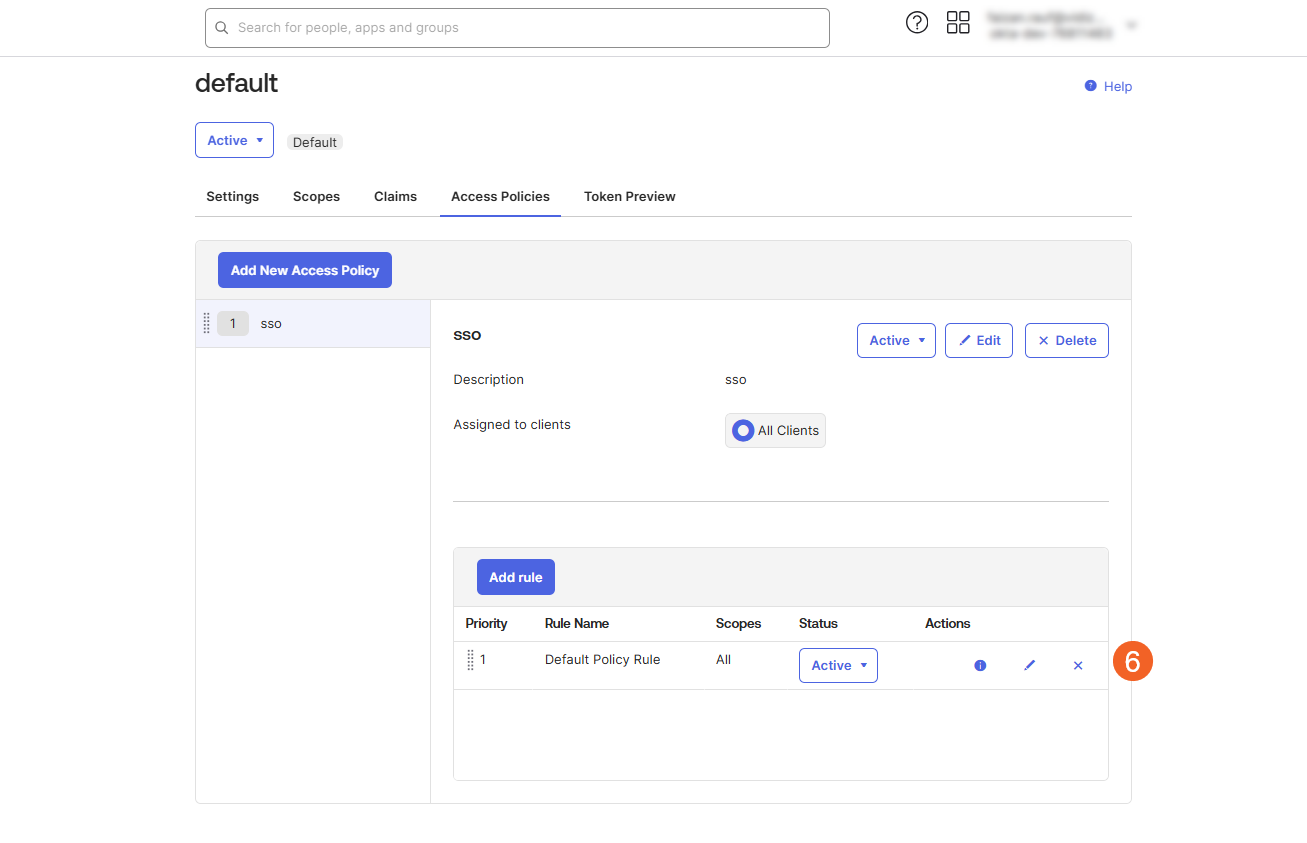
- Once saved, the created rule will appear under the Access Policies tab, associated with the respective policy.
Noting Parameters from Okta
- Client ID and Client Secret:
- Navigate to the General tab of the created application.
- Locate the Client Credentials section and copy the Client ID and Client Secret.Locate the Client Credentials section and copy the Client ID and Client Secret.
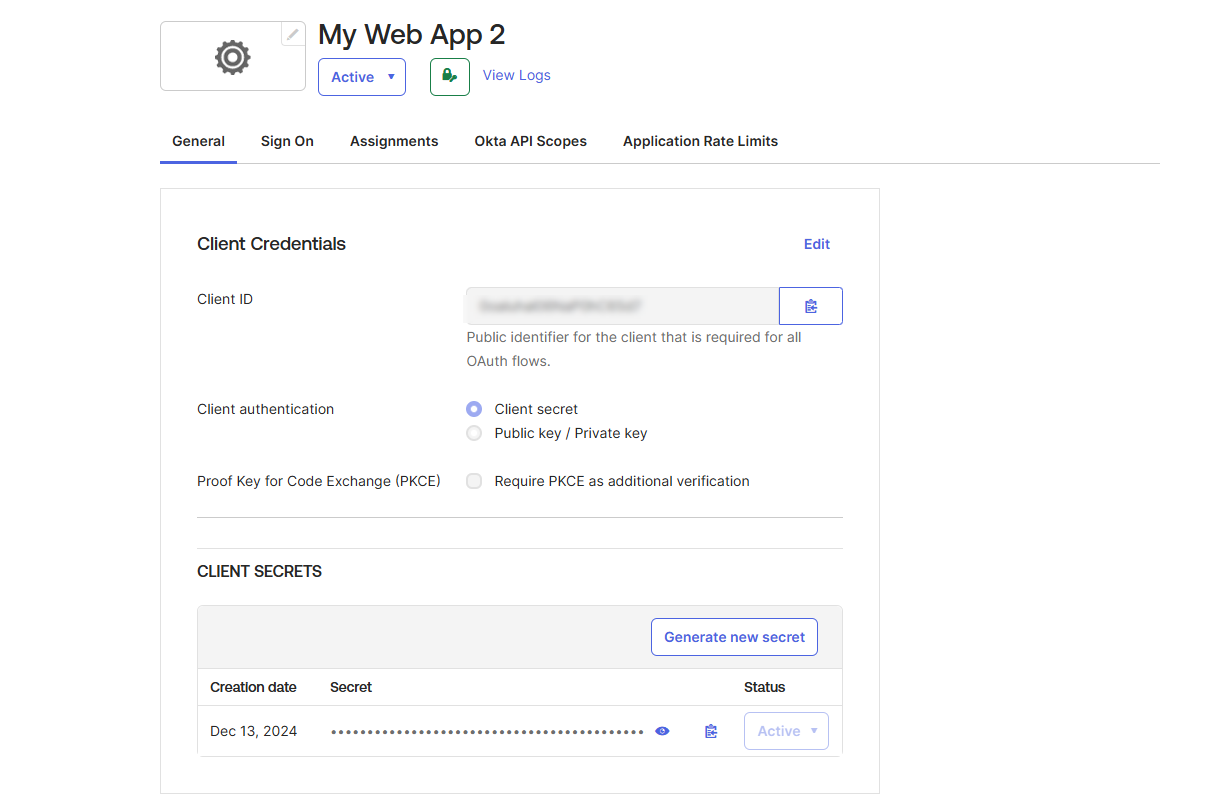
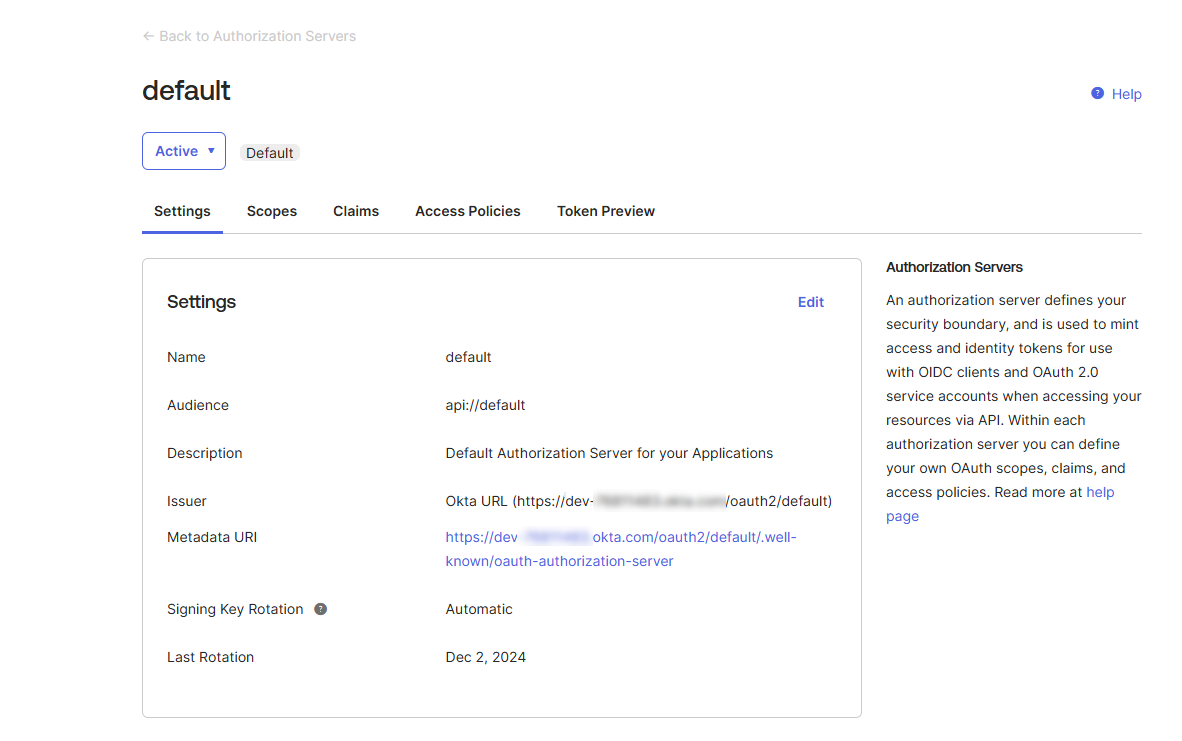
- Metadata URI:
- Go to Security > API.
- Under the Authorization Servers tab, find the Default Authorization Server and click Edit.
- From the Settings tab of the Default Authorization Server, locate and copy the Metadata URI.
Configuration in VIDIZMO
In your VIDIZMO portal follow the steps to configure okta app.
- Click on the navigation menu on top left corner.
- Expand Admin tab select Portal Settings.
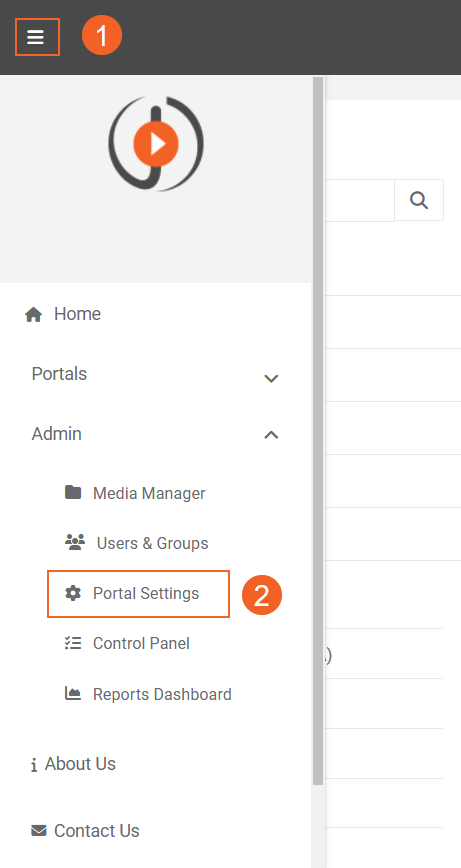
- On Portal Settings page click on the Apps tab.
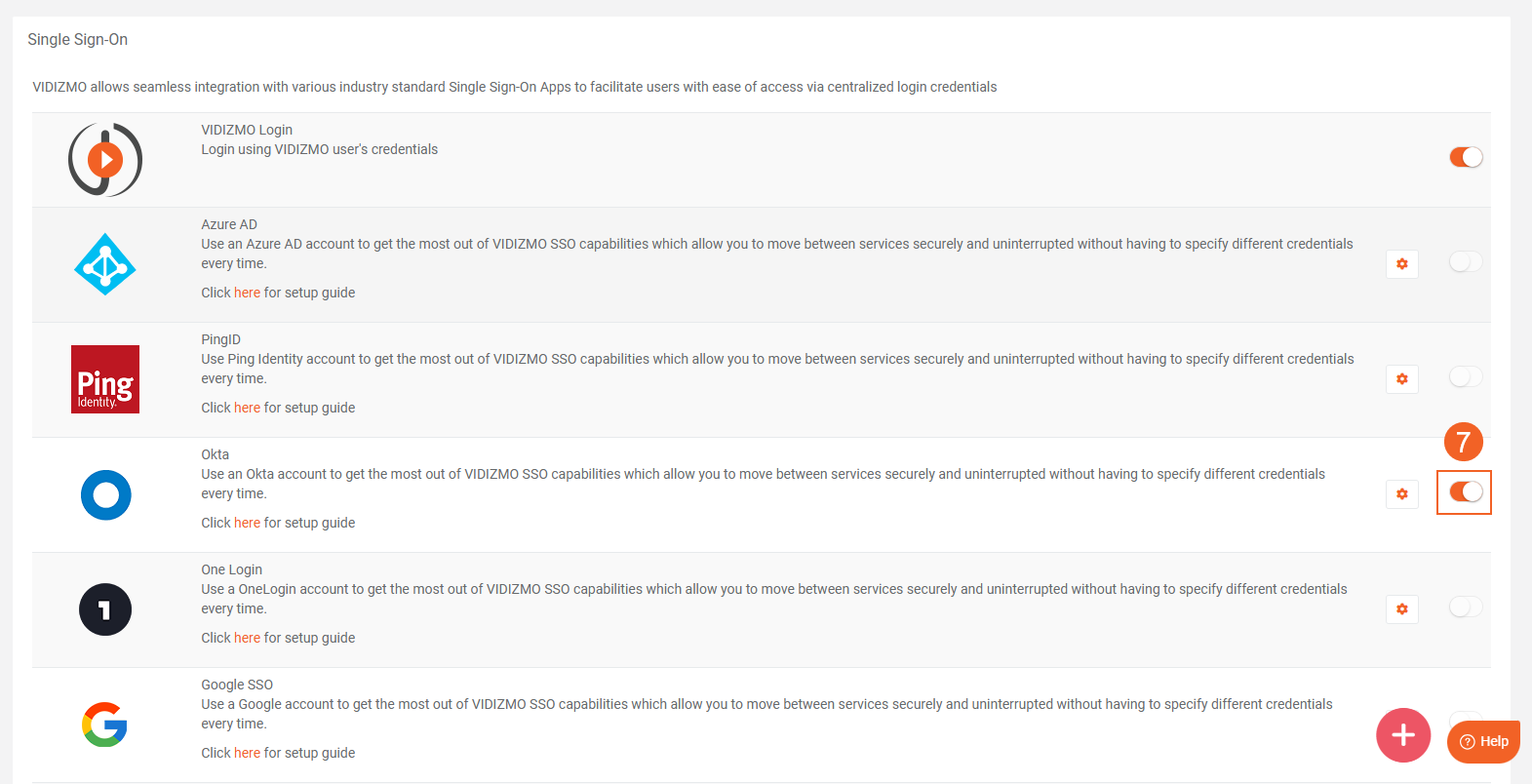
- Click on the Single Sign-On and Locate the Okta App.
- Click on the Settings icon.
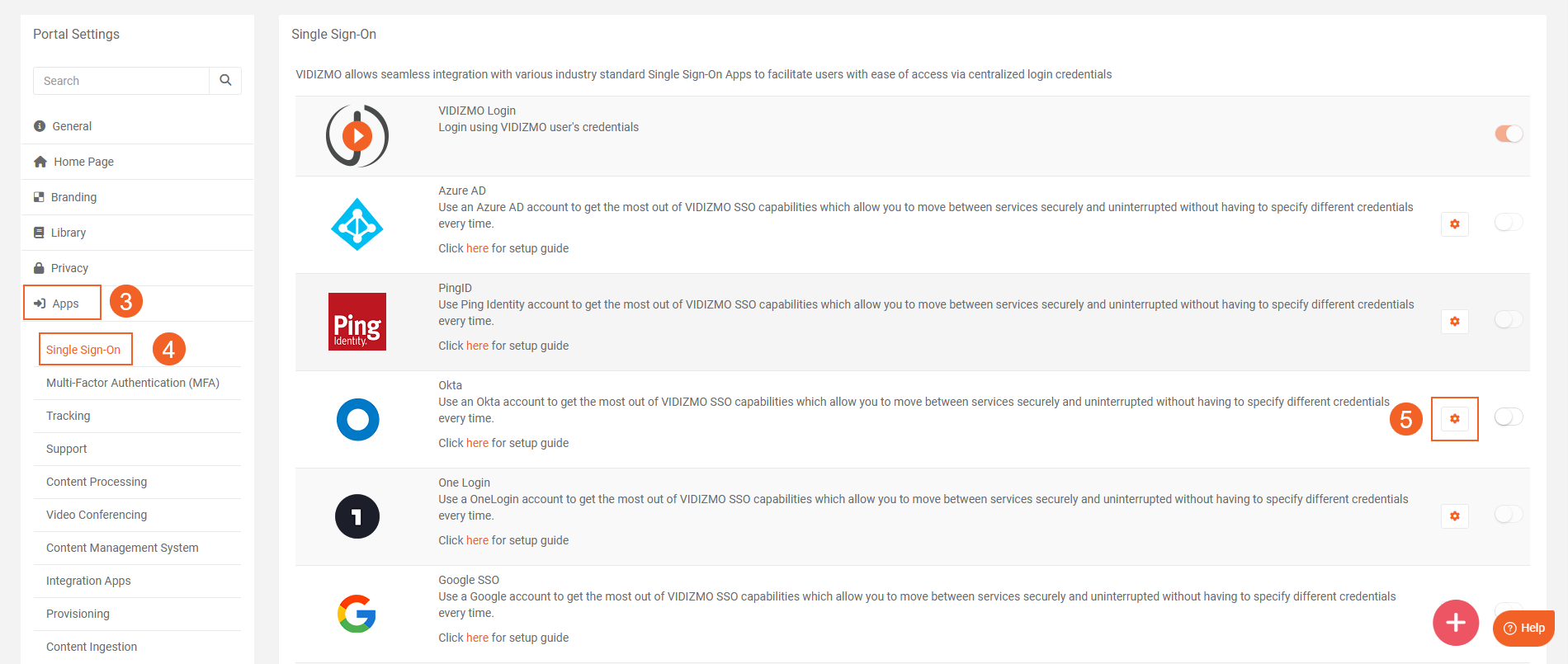
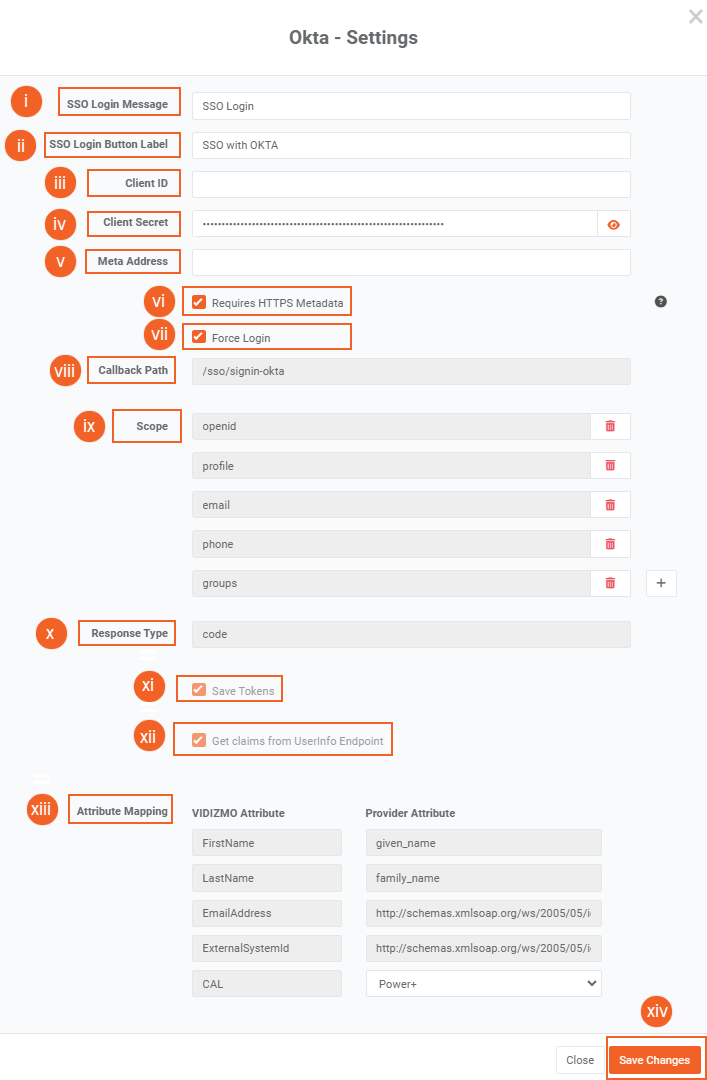
- After clicking on the Settings icon, a window will appear which offers various fields, each of which is explained below:
i. SSO Login Message: Enter here the message that you want to display on your portal login screen for Okta login.
ii. SSO Login Button Label: Text displayed on the login button.
iii. Client ID: This is a unique identifier for the client application. Enter the Client ID you noted earlier from Okta during the creation of the application.
iv. Client Secret: The client secret is used for accessing groups in your Identity Provider (IdP).Enter the Client secret you noted earlier from Okta during the creation of the application.
v. Meta Address: Enter the Metadata URI. If your Okta application is using:
- OIDC
The URL appears in this format: https://<yourOktaDomain>/oauth2/default/.well-known/openid-configuration
- OAuth
The URL appears in this format: https://<yourOktaDomain>/oauth2/default/.well-known/oauth-authorization-server
NOTE: Refer to the Okta developer documentation for updated endpoint information.
vi. Requires HTTPS Metadata: Select this check box to get metadata. When the request is handled for the first time, it tries to retrieve some metadata from the authorization server (also called an authority or issuer). This metadata, or discovery document in OpenID Connect terminology, contains the public keys and other details needed to validate tokens.
vii. Force Login: Select the checkbox to enable forced login and it will take you directly to Okta. When unchecked, it will not redirect automatically to the IdP and you will be required to sign in through your Portal's sign in screen.
viii. Callback Path: Specifies the callback location where the authorization will be sent to your Portal.
ix. Scope: A space-delimited list of scopes. OpenID Connect uses scope values to specify what access privileges are being requested for access tokens. The scopes associated with access tokens determine which claims are available when they are used to access the OIDC /userinfo endpoint. The following scopes are supported: openid, profile, email, phone, groups etc.
x. Response Type: Specifies the response type for OIDC authentication. Any combination of code, token, and id_token is used and is an opaque value that can be used to redeem tokens from the token endpoint. In our example, we have used "code" type. The code is returned if the response_type includes code. The code has a lifetime of 60 seconds.
xi. Save Tokens: API tokens have the same permissions as the user who creates them, and if the user permissions change, the API token permissions will also change.
xii. Get Claims From UserInfo Endpoint: This option returns claims about the authenticated end user if the UserInfo endpoint claims need to be obtained implicitly.
xiii. Attribute Mapping: Attribute Mapping allows you to map your attributes with the IDP's attributes.
- If multiple CAL (Client Access License) types are available in your VIDIZMO portal, you can select the desired CAL type. This selection will be automatically applied to all users who log in to the VIDIZMO portal using Okta SSO.
- Note that after the automatic sign-in and CAL assignment, the number of available CALs should be dynamically decreased and reflected consistently across all application screens displaying the remaining count, such as on the consumption screens.
xiv. Click on the button Save Changes.
A notification will appear stating Portal Information Updated Successfully.
- Click on the toggle button at the right-side of Okta to enable Okta SSO.
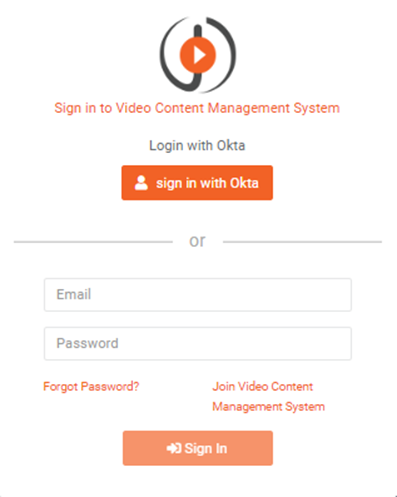
Result
Navigate to the Portal's login screen and you will see an option Login with Okta.
Read Next
How to Setup SAML-P SSO using Okta